top of page
Search


Qantas Faces Cybersecurity Incident: Up to 6 Million Customers Affected
Significant Customer Data Breach SYDNEY, Australia – July 3, 2025 – Australian national airline Qantas has officially confirmed it is...

Dark Hats
Jul 16, 20253 min read


Critical Zero-Day Vulnerability in Microsoft SQL Server Actively Exploited
[REDMOND, WA] – July 8, 2025 – Microsoft has released its monthly security update for July, addressing a total of 130 vulnerabilities...

Dark Hats
Jul 10, 20251 min read


Arrests Made in Connection with Major UK Retail Cyberattacks
[LONDON, UK] – July 10, 2025 – Authorities in the United Kingdom have made a significant breakthrough in the investigation into a series...

Dark Hats
Jul 10, 20251 min read


CISA Issues Urgent Warning for Actively Exploited Vulnerability in Microsoft Edge
# Urgent Directive: Critical Vulnerability in Microsoft Edge (CVE-2025-6554) ## CISA Issues Warning WASHINGTON, D.C. – July 3, 2025 ...

Dark Hats
Jul 3, 20252 min read


State-Sponsored Hackers Exploit Ivanti Zero-Days to Breach High-Value Networks
PARIS, France – July 3, 2025 – France's national cybersecurity agency, ANSSI, has released a detailed report today confirming that a...

Dark Hats
Jul 3, 20251 min read


🔐 Russia-Linked APT28 Launches Stealth Malware Attack Using Encrypted Messaging Channels
Executive Summary In a newly discovered cyber-espionage campaign, the notorious Russia-linked threat actor APT28 (also known as Fancy...
abdalsalam
Jun 25, 20252 min read


APT28 Deploys Sophisticated BEARDSHELL & COVENANT Malware via Encrypted Messaging
Overview: Ukraine's Computer Emergency Response Team (CERT-UA) has issued an urgent alert regarding a newly discovered cyber‑espionage...

Dark Hats
Jun 25, 20252 min read


Iranian Hackers Target Israeli Home Cameras to Refine Missile Strikes, Authorities Warn
Israeli cybersecurity officials have issued a critical warning to the public, revealing that Iranian state-sponsored hackers are...

Dark Hats
Jun 21, 20252 min read

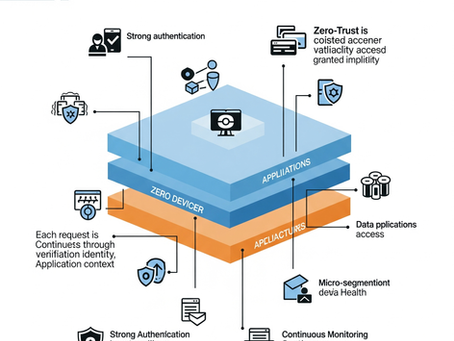
The Imperative of Zero-Trust Architectures in Modern Networks
The traditional "castle-and-moat" security model is proving ineffective against today's sophisticated threats, leading to a widespread...

Dark Hats
Jun 21, 20251 min read


Supply Chain Attacks Leverage Open-Source Software
A concerning trend has emerged in the cybersecurity landscape, with threat actors increasingly focusing on the software supply chain,...

Dark Hats
Jun 21, 20251 min read


Massive Leak: 16 Billion Passwords Exposed
Summary: A staggering 16 billion login credentials, including emails and passwords from major platforms such as Apple, Google, and...

Dark Hats
Jun 21, 20251 min read
bottom of page